Книга: Mastering VMware® Infrastructure3
Configuring Virtual Switch Security
Even though the vSwitches created in the VMkernel are considered to be “dumb switches”, they can be configured with vSwitch security policies to enhance or ensure Layer 2 security. Security policies can be applied at the vSwitch or at the lower-level connection types configured on a vSwitch and include the following three security options:
? Promiscuous Mode
? MAC Address Changes
? Forged Transmits
Applying a security policy to the vSwitch is effective, by default, for all connection types within the switch. However, if a connection type, or port group, is configured with a competing security policy, it will override the policy set at the vSwitch. As in the example in Figure 3.35, if a vSwitch is configured with a security policy that rejects the use of MAC address changes but a virtual machine port group on the switch is configured to accept MAC address changes, then any virtual machines connected to that port group will be allowed to communicate even though it is using a MAC address that differs from what is configured in its VMX file.
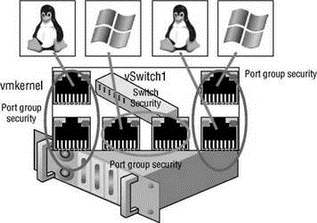
Figure 3.35 Security policies at the switch level are effective by default for all connection types on the switch. Security policies at the connection type (port group) level override the policy set at the virtual switch.
The default security profile for a vSwitch, shown in Figure 3.36, is set to reject Promiscuous mode and to accept MAC address changes and Forged transmits.
- Configuring networking for Hyper-V
- Chapter 3: Creating and Managing Virtual Networks
- Chapter 3 Creating and Managing Virtual Networks
- Интегрированная безопасность (NT Integrated Security)
- Chapter 5 Installing and Configuring VirtualCenter 2.0
- 2.2.5. ATM Switching
- Глава 2 Виртуальные машины Virtual PC 2004
- 7.7.2. mod_security
- Choosing, Configuring, and Installing the Boot Loader
- Configuring Wireless Networks
- Configuring X
- Using Fedora's switchdesk Client




