Книга: Mastering VMware® Infrastructure3
About the Author
Разделы на этой странице:
About the Author
Chris McCain is an author, consultant, and trainer who focuses on VMware and Microsoft products. As an owner in the National IT Training & Certification Institute (NITTCI) and a partner at viLogics, he has been instrumental in providing training to thousands of IT professionals and consulting to some of the largest companies in the world. Chris has provided support in the form of training and consulting to companies such as Microsoft, VMware, IBM, Dell, Credit Suisse, Intel, and others.
In addition to virtualization, Chris offers expertise across a variety of technologies, including Active Directory, public key infrastructure, SQL Server 2005, IPSec, SharePoint, and more.
Chris holds a long list of industry certifications, including VCP, VCI, MCT, MCITP, MCSE: Security, and CISSP, to name a few. His other book credits include contributing to the Microsoft Office SharePoint Server 2007 Administrator's Companion by Microsoft Press, the MCITP Self-Paced Training Kit (Exam 70-647) by Microsoft Press, and the Mike Meyers Passport Certification Series: Exam 70-293 by McGraw-Hill.
As an IT professional, Chris is dedicated to providing value to the community as a whole through his personal blogs at http://www.GetYourNerdOn.com. Visit the site to find a growing library of videos and commentary on IT technologies across Microsoft, VMware, and more.
Introduction
For the past several years, the buzzword exciting the information technology community has been security: network security, host security, application security, just about any type of security imaginable. There is a new buzzword around the information technology world and it's rapidly becoming the most talked about technology since the advent of the client/server network. That buzzword is virtualization.
Virtualization is the process of implementing multiple operating systems on the same set of physical hardware to better utilize the hardware. Companies with strong plans to implement virtualized computing environments look to gain many benefits, including easier systems management, increased server utilization, and reduced datacenter overhead. Traditional IT management has incorporated a one-to-one relationship between the physical servers implemented and the roles they play on the network. When a new database is to be implemented, we call our hardware vendor of choice and order a new server with specifications to meet the needs of the database. Days later we may order yet another server to play the role of a file server. This process of ordering servers to fill the needs of new network services is oftentimes consuming and unnecessary given the existing hardware in the datacenter. To ensure stronger security, we separate services across hosts to facilitate the process of hardening the operating system. We have learned over time that the fewer the functions performed by a server, the fewer the services that are required to be installed, and, in turn, the easier it is to lock down the host to mitigate vulnerabilities. The byproduct of this separation of services has been the exponential growth of our datacenters into large numbers of racks filled with servers, which in most cases are barely using the hardware within them.
Virtualization involves the installation of software commonly called a hypervisor. The hypervisor is the virtualization layer that allows multiple operating systems to run on top of the same set of physical hardware. Figure I.1 shows the technological structure of a virtualized computing environment. Virtual machines that run on top of the hypervisor can run almost any operating system, including the most common Windows and Linux operating systems found today as well as legacy operating systems from the past.
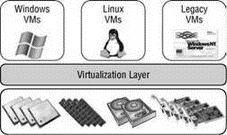
Figure I.1 The process of virtualization involves a virtualization layer called a hypervisor that separates the physical hardware from the virtual machines. This hypervisor manages the virtual machines' access to the underlying hardware components.
For those just beginning the journey to a virtual server environment and for those who have already established their virtual infrastructures, the reasons for using virtualization can vary. Virtualization offers many significant benefits, including server consolidation, rapid server provisioning, new options in disaster recovery, and better opportunities to maintain service-level agreements (SLAs), to name a few. Perhaps the most common reason is server consolidation.
Most servers in a datacenter are performing at less than 10 percent CPU utilization. This leaves an overwhelming amount of processing power available but not accessible because of the separation of services. By virtualizing servers into virtual machines running on a hypervisor, we can better use our processors while reducing rack space needs and power consumption in the datacenter.
Depending on the product used to virtualize a server environment, there are many more benefits to virtualization. Think of the struggles IT professionals have had throughout the years and you'll gain a terrific insight into why virtualization has become such a popular solution. The simple process of moving a server from a datacenter in Tampa, Florida, to a datacenter in Atlanta, Georgia, is a good example of a common pain point for IT pros. The overhead of removing an 80-pound server from a rack, boxing it, shipping it, unboxing it, and placing it back into another rack is enough to make you want to virtualize. With virtual machines this same relocation process can be reduced to simply copying a directory to an external media device, shipping the external media device, and copying the directory back to another ESX implementation. Other methods, such as virtual machine replication and full and delta images of virtual machines, can be taken with third-party tools.
Although a handful of products have emerged for enterprise-level virtualization, this book provides all of the details an IT professional needs to design, deploy, manage, and monitor an environment built on the leading virtualization product, VMware Infrastructure 3.
What Is Covered in This Book
This book is written with a start-to-finish approach to installing, configuring, managing, and monitoring a virtual environment using the VMware Infrastructure 3 (VI3) product suite. The book begins by introducing the VI3 product suite and all of its great features. After introducing all of the bells and whistles, this book details an installation of the product and then moves into configuration. Upon completion of the installation and configuration, we move into virtual machine creation and management, and then into monitoring and troubleshooting. This book can be read from cover to cover to gain an understanding of the VI3 product in preparation for a new virtual environment. Or it can also be used as a reference for IT professionals who have begun their virtualization and want to complement their skills with real-world tips, tricks, and best practices as found in each chapter.
This book, geared toward the aspiring and the practicing virtualization professional, provides information to help implement, manage, maintain, and troubleshoot an enterprise virtualization scenario. As an added benefit we have included four appendices: one offering solutions to Master It problems, another detailing common Linux and ESX commands, another discussing some of the more popular tools and third-party products that can be used to facilitate virtual infrastructure management, and another describing best practices for VI3.
Here is a glance at what's in each chapter:
Chapter 1: Introducing VMware Infrastructure 3 begins with a general overview of all the products that make up the VI3 product suite. VMware has created a suite with components to allow for granular licensing and customization of features for each unique deployment.
Chapter 2: Planning and Installing ESX Server looks at planning the physical hardware, calculating the return on investment, and installing ESX Server 3.5 both manually and in an unattended fashion.
Chapter 3: Creating and Managing Virtual Networks dives deep into the design, management, and optimization of virtual networks. In addition, it initiates discussions and provides solutions on how to integrate the virtual networking architecture with the physical network architecture while maintaining network security.
Chapter 4: Creating and Managing Storage Devices provides an in-depth overview of the various storage architectures available for ESX Server 3.5. This chapter discusses fibre channel, iSCSI, and NAS storage design and optimization techniques as well as the new advanced storage features like round-robin load balancing, NPIV, and Storage VMotion.
Chapter 5: Installing and Configuring VirtualCenter 2.0 offers an all-encompassing look at VirtualCenter 2.5 as the brains behind the management and operations of a virtual infrastructure built on the VI3 product suite. From planning, installing, and configuring, this chapter covers all aspects of VirtualCenter 2.5.
Chapter 6: Creating and Managing Virtual Machines introduces the practices and procedures involved in provisioning virtual machines through VirtualCenter 2.5. In addition, you'll be introduced to timesaving techniques, virtual machine optimization, and best practices that will ensure simplified management as the number of virtual machines grows larger over time.
Chapter 7: Migrating and Importing Virtual Machines continues with more information about virtual machines but with an emphasis on performing physical-to-virtual (P2V) and virtual-to-virtual (V2V) migrations in the VI3 environment. This chapter provides a solid, working understanding of the VMware Converter Enterprise tool and offers real-world hints at easing the pains of transitioning physical environments into virtual realities.
Chapter 8: Configuring and Managing Virtual Infrastructure Access Controls covers the security model of VI3 and shows you how to manage user access for environments with multiple levels of system administration. The chapter shows you how to use Windows users and groups in conjunction with the VI3 security model to ease the administrative delegation that comes with enterprise-level VI3 deployments.
Chapter 9: Managing and Monitoring Resource Access provides a comprehensive look at managing resource utilization. From individual virtual machines to resource pools to clusters of ESX Server hosts, this chapter explores how resources are consumed in VI3. In addition, you'll get details on the configuration, management, and operation of VMotion and Distributed Resource Scheduler (DRS).
Chapter 10: High Availability and Business Continuity covers all of the hot topics regarding business continuity and disaster recovery. You'll get details on building highly available server clusters in virtual machines as well as multiple suggestions on how to design a backup strategy using VMware Consolidated Backup and other backup tools. In addition, this chapter discusses the use of VMware High Availability (HA) as a means of providing failover for virtual machines running on a failed ESX Server host.
Chapter 11: Monitoring Virtual Infrastructure Performance takes a look at some of the native tools in VI3 that allow virtual infrastructure administrators the ability to track and troubleshoot performance issues. The chapter focuses on monitoring CPU, memory, disk, and network adapter performance across ESX Server 3.5 hosts, resource pools, and clusters in VirtualCenter 2.5.
Chapter 12: Securing a Virtual Infrastructure covers different security management aspects, including managing direct ESX Server access and integrating ESX Servers with Active Directory.
Chapter 13: Configuring and Managing ESXi finishes the book by looking at the future of the hypervisor in ESXi. This chapter covers the different versions of ESXi and how they are managed.
Appendix A: Solutions to the Master It Problems offers solutions to the Master It problems in each chapter.
Appendix B: Common Linux and ESX Commands focuses on navigating through the Service Console command line and performing management, configuration, and troubleshooting tasks.
Appendix C: Third-Party Virtualization Tools discusses some of the virtualization tools available from third-party vendors.
Appendix D: Virtual Infrastructure 3 Best Practices serves as an overview of the design, deployment, management, and monitoring concepts discussed throughout the book. It is designed as a quick reference for any of the phases of a virtual infrastructure deployment.
The Mastering Series
The Mastering series from Sybex provides outstanding instruction for readers with intermediate and advanced skills, in the form of top-notch training and development for those already working in their field and clear, serious education for those aspiring to become pros. Every Mastering book includes:
? Real-World Scenarios, ranging from case studies to interviews, that show how the tool, technique, or knowledge presented is applied in actual practice
? Skill-based instruction, with chapters organized around real tasks rather than abstract concepts or subjects
? Self-review test questions, so you can be certain you're equipped to do the job right
The Hardware Behind the Book
Due to the specificity of the hardware for installing VMware Infrastructure 3, it might be difficult to build an environment in which you can learn by implementing the exercises and practices detailed in this book. It is possible to build a practice lab to follow along with the book; however, the lab will require very specific hardware and can be quite costly. Be sure to read Chapter 2 before attempting to construct any type of environment for development purposes.
For the purpose of writing this book, we used the following hardware configuration:
? Three Dell PowerEdge 2850 servers for ESX
? Two Intel Xeon 2.8GHz processors
? 4GB of RAM
? Two hard drives in RAID-1 Array (Mirror)
? QLogic 23xx iSCSI HBA
? Four Gigabit Ethernet adapters: two on-board, two and two in a dual-port expansion card
? QLogic 40xx iSCSI HBA
? EMC CX-300 storage device
? Two Brocade fibre channel switches
? LeftHand Networks iSCSI virtual storage appliance
As we move through the book, we'll provide diagrams to outline the infrastructure as it progresses.
Who Should Buy This Book
This book is for IT professionals looking to strengthen their knowledge of constructing and managing a virtual infrastructure on VMware Infrastructure 3. While the book can be helpful for those new to IT, there is a strong set of assumptions made about the target reader:
? A basic understanding of networking architecture
? Experience working in a Microsoft Windows environment
? Experience managing DNS and DHCP
? A basic understanding of how virtualization differs from traditional physical infrastructures
? A basic understanding of hardware and software components in standard x86 and x64 computing
How to Contact the Author
I welcome feedback from you about this book or about books you'd like to see from me in the future. You can reach me by writing to [email protected] or by visiting my blog at http://www.getyournerdon.com.
- Acknowledgments
- About the Author
- Chapter 1 Introducing VMware Infrastructure 3
- Chapter 2 Planning and Installing ESX Server
- Chapter 3 Creating and Managing Virtual Networks
- Chapter 4 Creating and Managing Storage Devices
- Chapter 5 Installing and Configuring VirtualCenter 2.0
- Chapter 6 Creating and Managing Virtual Machines
- Chapter 7 Migrating and Importing Virtual Machines
- Chapter 8 Configuring and Managing Virtual Infrastructure Access Controls
- Chapter 9 Managing and Monitoring Resource Access
- Chapter 10 High Availability and Business Continuity
- Chapter 11 Monitoring Virtual Infrastructure Performance
- Chapter 12 Securing a Virtual Infrastructure
- Chapter 13 Configuring and Managing ESXi
- Appendix A The Bottom Line
- Appendix B Common Linux and ESX Commands
- Appendix C Third-Party Virtualization Tools
- Appendix D VMware Infrastructure 3 Best Practices
- Содержание книги
- Популярные страницы
- About the author
- CHAPTER 5 On the Internet
- The DISPLAY Processor
- Before You Begin the Installation
- The Computer Icon
- Use Essential Commands from the
- Using the Text Editors
- Browsing the Internet
- Laying the Foundation: The localhost Interface
- Beyond the Network and Onto the Internet
- The SSH Tools
- Setting a Password for the MySQL Root User




