Книга: Mastering VMware® Infrastructure3
Using VCB for Full Virtual Machine Backups
Разделы на этой странице:
Using VCB for Full Virtual Machine Backups
As we mentioned briefly in the opening section, VCB is a framework for backup that integrates with third-party backup software. It is a series of scripts that performs online, LAN-free backups of virtual machines or virtual machine files.
VCB for Fibre Channel… and iSCSI Too!
When first released, VCB was offered as a fibre channel-only solution; VMware did not support VCB used over an iSCSI storage network. The latest release of VCB offers support for use with iSCSI storage.
The requirements for VCB 1.1 include:
? A physical server running Windows Server 2003 Service Pack 1.
? If using Windows Server 2003 Standard Edition, the VCB server must be configured not to automatically assign drive letters using diskpart to execute automount disable and automount scrub.
? Network connectivity for access to VirtualCenter.
? Fibre channel HBA with access to all SAN LUNs where virtual machine files are stored.
? Installation of the third-party software prior to installing and configuring VCB.
VCB on Fibre Channel Without Multipathing
The VCB proxy requires a fibre channel HBA to communicate with fibre channel SAN LUNs regarding backup processes. VCB does not, however, support multiple HBAs or multipathing software like EMC PowerPath. Insert only one fibre channel HBA into a VCB proxy.
Figure 10.43 looks at the VCB components and architecture.
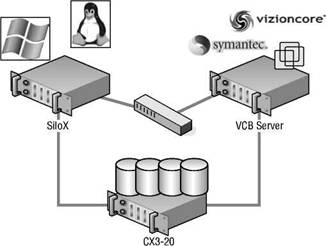
Figure 10.43 A VCB deployment relies on several communication mediums, including network access to VirtualCenter and fibre channel access to all necessary SAN LUNs.
VMware regularly tests third-party support for VCB, and, as a result, the list of supported backup products continues to change. As of this writing, the following products were listed as backup products for which VMware provides integration scripts:
? EMC NetWorker
? Symantec Backup Exec
? Tivoli Storage Manager
? Veritas NetBackup
In addition to these four products, VMware lists the following products as having created integrations to allow their products to capitalize on the VCB framework:
? Vizioncore vRanger Pro, formerly ESXRanger Pro
? Certificate Associates (CA) BrightStor ARCServe
? CommVault Galaxy
? EMC Avamar
? HP Data Protector versions 5.5 and 6
Be sure to regularly visit VMware's website to download and review the PDF at http://www.vmware.com/pdf/vi_3backupguide.pdf.
Although considered a framework for backup, VCB can actually be used as a backup product. However, it lacks the nice scheduling and graphical interface features of third-party products like Vizioncore vRanger Pro. Two of the more common VCB commands, shown in Figures 10.44 and 10.45, are:
? vcbVmName: This command enumerates the various ways a virtual machine can be referenced in the vcbMounter. Here's an example:
vcbVmName -h 172.30.0.120 -u administrator -p Sybex!! -s ipaddr:172.30.0.24
where
? -h <VirtualCenter Server name or IP address>
? -u <VirtualCenter username>
? -p <VirtualCenter user password>
? -s ipaddr: <IP address of virtual machine to backup>
? vcbMounter:
? -h <VirtualCenter Server name or IP address>
? -u <VirtualCenter username>
? -p <VirtualCenter user password>
? -a <name | ipaddr | moref | uuid>: <attribute value>
? -t [fullvm | file]
? -r <Backup directory on VCB proxy>
VCB Proxy Backup Directory
When specifying the VCB backup directory using the -r parameter, do not specify an existing folder. For example, if a backup directory E:VCBBackups already exists and a new backup should be stored in a subdirectory named Server1, then specify the subdirectory without creating it first. In this case, the -r parameter might read as follows:
-r E:VCBBackupsServer1
The vcbMounter will create the new directory as needed. If the directory is created first, an error will be thrown at the beginning of the backup process. The error will state that the directory already exists.
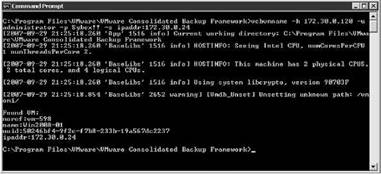
Figure 10.44 The vcbVmName command enumerates the various virtual machine identifiers that can be used when running the VCB command.
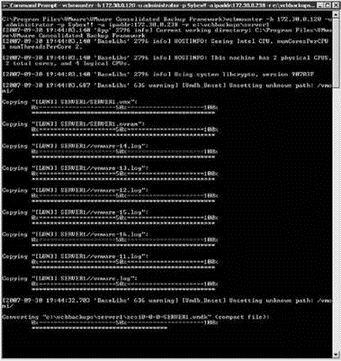
Figure 10.45 The vcbMounter command can be used to perform full virtual machines backups or file-level backups for Windows virtual machines.
When VCB performs a full backup of a virtual machine, it engages the VMware snapshot functionality to quiesce the file system and perform the backup. Remember that snapshots are not complete copies of data. Instead, a snapshot is the creation of a differencing file (or redo log) to which all changes are written. When the vcbMounter command is used, a snapshot is taken of the virtual machine, as shown in Figure 10.46.
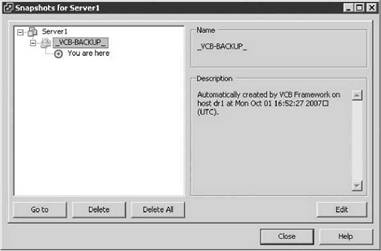
Figure 10.46 The snapshots created by VCB can be viewed in the snapshot manager of a virtual machine.
Any writes that occur during the backup are done to the differencing file. Meanwhile, VCB is busy making a copy of the VMDK, which is now read-only for the duration of the backup job. Figure 10.47 details the full virtual machine backup process. Once the backup job is completed, the snapshot is deleted, forcing all writes that occurred to the differencing file to be written to the virtual machine disk file.
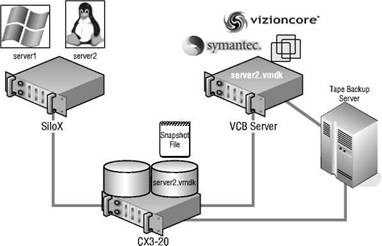
Figure 10.47 Performing a full virtual machine backup utilizes the VMware snapshot functionality, which ensures that an online backup is correct as of that point in time.
Snapshots and VMFS Locking
Snapshots grow by default in 16MB increments, and for the duration of time it takes to grow a snapshot, a lock is held on the VMFS volume so the respective metadata can be updated to reflect the change in the snapshot. For this reason, do not instantiate a snapshot for many virtual machines at once. Although the lock is held only for the update to the metadata, the more virtual machines trying at the same time, the greater the chance of contention on the VMFS metadata. From an IT standpoint, this factor should drive your backup strategy to perform backups of many virtual machines only if the virtual machine files have been located on separate VMFS volumes.
Perform the following steps to perform a full virtual machine backup using VCB:
1. Log in to the backup proxy where VCB is installed.
2. Open a command prompt and change directories to the C:Program FilesVMwareVMware Consolidated Backup Framework directory.
3. Use the vcbVmName tool to enumerate virtual machine identifiers. At the command prompt, type:
vcbVmName <IP or name of VirtualCenter> -u <username> -p <password> -s ipaddr:<IP address of virtual machine to backup>
4. From the results of running the vcbVmName tool, select which identifier to use (moref, name, uuid, or ipaddr) in the vcbMounter command.
5. At the command prompt, type:
VcbMounter -h <IP or name of VirtualCenter> -u <username> -p <password> -a ipaddr:<IP address of virtual machine to backup> -t fullvm -r <VCB proxy backup directory>
Once the backup is complete, a list of the files can be reviewed in the directory provided in the backup script. Figure 10.48 shows the files created as part of the completed full backup of a virtual machine named Server1.
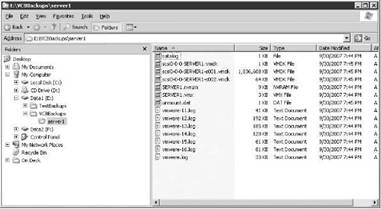
Figure 10.48 A full virtual machine backup using VCB creates a directory of files that include a configuration file (VMX), log files, and virtual machine hard drives (VMDK), among others.
Redundant Paths
Let's look at an example of a VCB backup proxy with a single QLogic fibre channel HBA that is connected to a single fibre channel switch connected to two storage processors on the storage device. This configuration results in two different paths being available to the VCB server. The image here shows that a VCB server with a single HBA will find LUNs twice because of the redundancy at the storage-processor level:
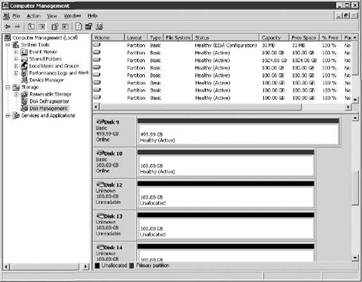
When Disk Management shows this configuration for the older versions of VCB, it presents a problem that causes every backup attempt to fail. For the pre-VCB 1.0.3 versions, the LUNs identified as Unknown and Unreadable must be disabled in Disk Management. The option to disable is located on the properties of a LUN. The following image displays the General tab of LUN properties from Disk Management where a path to a LUN can be disabled. To remove the redundant unused paths from Computer Management, the Device Usage drop-down list should be set to Do not use this device (disable).
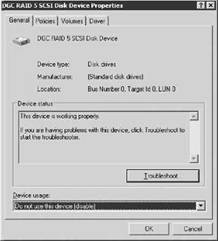
With redundant paths disabled, this will, of course, present a problem when a LUN trespasses to another storage processor. This requires a path to the LUN that is likely disabled.
- Forced writes - палка о двух концах
- Forced Writes
- Chapter 7. The state machine
- Chapter 5 Installing and Configuring VirtualCenter 2.0
- Chapter 15. Graphical User Interfaces for Iptables
- What NAT is used for and basic terms and expressions
- Caveats using NAT
- Example NAT machine in theory
- Using Double Quotes to Resolve Variables in Strings with Embedded Spaces
- Information request
- SCTP Generic header format
- What is needed to build a NAT machine




