Книга: Fedora™ Unleashed, 2008 edition
SSH Access to a Database
SSH Access to a Database
Two types of remote database access scenarios are briefly discussed in this section. In the first scenario, the user directly logs in to the database server through SSH (to take advantage of the security benefits of encrypted sessions) and then starts a program on the server to access the database. In this case, shown in Figure 18.4, the database client is running on the database server itself.
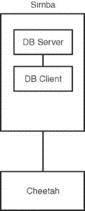
FIGURE 18.4 The user logs in to the database server located on host simba from the workstation (host cheetah). The database client is running on simba.
In the other scenario, shown in Figure 18.5, the user logs in to a remote host through SSH and starts a program on it to access the database, but the database is actually running on a different system. Three systems are now involved: the user's workstation, the remote host running the database client, and the remote host running the database server.
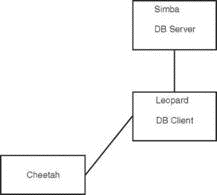
FIGURE 18.5 The user logs in to the remote host leopard from the workstation (host cheetah) and starts a database client on leopard. The client on leopard then connects to the database server running on host simba. The database client is running on leopard.
The important thing to note in Figure 18.5 is the middleman system leopard. Although the client is no longer running on the database server itself, it isn't running on the user's local workstation, either.
- Database Clients
- The PostgreSQL Command-Line Client
- Практическая работа 53. Запуск Access. Работа с объектами базы данных
- Информация заголовочной страницы (Database header)
- Database dialect
- DATABASE CACHE SIZE
- Возможности SSH
- Configure Access Control
- Запуск Access. Открытие учебной базы данных Борей
- 5.3. Протокол SSH
- 5.3.2. Основные параметры конфигурации сервера SSH
- Листинг 5.1. Файл конфигурации sshd




