Книга: Mastering VMware® Infrastructure3
Managing and Configuring the Service Console Firewall
Managing and Configuring the Service Console Firewall
The configuration of the ESX Server's firewall is one area that VMware has made very easy. The firewall is based on IP tables, a firewall technology readily available on most Linux distributions. Working with IP tables is not for the uninitiated. But, with the esxcfg-firewall command-line utility, creating only those firewall rules necessary for proper ESX functionality is easy.
The default setup for the Service Console firewall is very secure. For both incoming and outgoing connections, only those ports necessary for management of the virtual machines and the ESX Server are open. This default mode of operation is High security. The other two modes of operation are Medium, which doesn't block outgoing ports, and Low, which doesn't block ingoing or outgoing ports. Some default ports open when using High are:
? 902 — VI Client connections
? 903 — Virtual Machine desktop connection
? 80/443 — Web browser connections
? 22 — ssh client connections
? 27000/27010 — License Server, if the ESX Server is managed by VirtualCenter
As shown in Figure 12.20, there are several other ports, having mostly to do with Common Information Model (CIM). CIM allows monitoring of many aspects of the hardware and storage of an ESX Server.
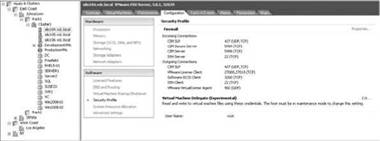
Figure 12.20 Ports open on a default installation of ESX 3.X
When you consider opening a new port, you can use the VI Client connected to VirtualCenter or the Service Console command esxcfg-firewall. Most of the time it is easy to open predefined ports with the VI Client, but in some cases, you might need to open a port for a lesser-known service or process, such as monitoring agents.
Service Console Firewall Services
ESX server has an XML file, /etc/vmware/firewall/services.xml, that defines those services used most often on an ESX Server and that are shown in the VI Client in the Security Profile. VMware does not support editing this file to add your own services.
Monitoring the firewall's configuration is an important step in auditing access to an ESX Server. As shown in Figure 12.20, using the VI Client is one way to monitor currently open ports on the firewall. In some cases, though, newly opened ports will not show up using the VI Client. The best way to audit currently open ports and the services using them is to use esxcfg-firewall -q. This listing is always accurate if user access has been restricted, as demonstrated earlier in this chapter.
Perform these steps to audit the current firewall settings:
1. Log into the Service Console as root.
2. Type the command esxcfg-firewall -q as shown in Figure 12.21.
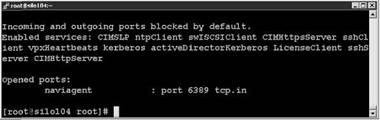
Figure 12.21 Auditing the Service Console firewall
3. Check that the server is blocking incoming and outgoing ports (High security). Check that only needed services ports have been enabled, and check that only necessary ports for added agents have been opened.
Use the esxcfg-firewall command to open ports defined in the services.xml file or those not listed in the profile.
Follow these steps to enable the firewall for locally defined services:
1. Log into the Service Console as root.
2. Type the command esxcfg-firewall -s to list possible services.
3. Once the service name has been located, type esxcfg-firewall -q service_name to check the firewall's port status.
4. Type esxcfg-firewall -e service name to enable the firewall port.
5. Type esxcfg-firewall -q service name to verify the port status as shown in Figure 12.22.
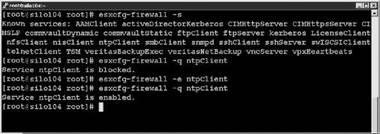
Figure 12.22 Enabling a firewall port for a predefined service
If you need to open a port for an agent or other third-party application not listed in services .xml, the esxcfg-firewall command still does that job, but the administrator has to know exactly what the agent or application needs. One example, the Dell OpenManage Server Agent, needs a specific port open to communicate with the OpenManage Web Administrative console. The command esxcfg-firewall -o 1311, tcp, in,OpenManageRequest opens the needed port. Breaking down the command:
? -o opens the port (-c would close the port).
? 1311 is the port to be opened.
? tcp is the protocol to be used.
? in specifies incoming traffic.
? OpenManageRequest is the name of the agent or service.
Perform the following steps to open a port for an agent or application not included in the default firewall services list:
1. Log into the Service Console as root.
2. Type esxcfg-firewall -o port, tcp or udp, in or out, name as shown in Figure 12.23.
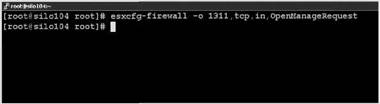
Figure 12.23 Enabling a firewall port for an unlisted service or agent
3. Type esxcfg-firewall -q to verify the status of the port as shown in Figure 12.24.
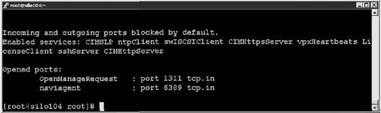
Figure 12.24 Verifying the status of the newly opened port
Once the firewall changes have been made, you still have to install the agent or application and test your connectivity. If at some point you want to close a port that is no longer needed, esxcfg-firewall does the trick.
Perform the following steps to limit ssh connections to specific users:
1. Log into the Service Console as root.
2. Type esxcfg-firewall -q to check the status and port number as shown in Figure 12.25.
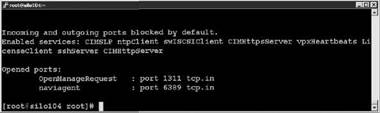
Figure 12.25 Verifying the status of the port to be closed
3. Type esxcfg-firewall -c port, tcp or udp, in or out, name as shown in Figure 12.26.
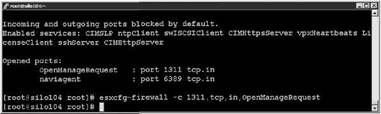
Figure 12.26 Closing the firewall port for an unlisted service or agent
4. Verify that the port is closed as shown in Figure 12.27.
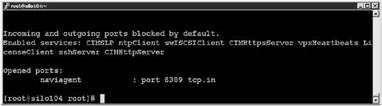
Figure 12.27 Confirming the closing of the firewall port
- Разработка приложений баз данных InterBase на Borland Delphi
- 4.4.4 The Dispatcher
- Open Source Insight and Discussion
- Introduction to Microprocessors and Microcontrollers
- About the author
- Chapter 6. Traversing of tables and chains
- Chapter 7. The state machine
- Chapter 8. Saving and restoring large rule-sets
- Chapter 11. Iptables targets and jumps
- Chapter 5 Installing and Configuring VirtualCenter 2.0
- Chapter 13. rc.firewall file
- Chapter 16. Commercial products based on Linux, iptables and netfilter




