Книга: Windows Server 2012 R2 Storage, Security, & Networking Pocket Consultant
Analyzing, reviewing, and applying security templates
Analyzing, reviewing, and applying security templates
As stated previously, you use the Security Configuration And Analysis snap-in to apply templates and to compare the settings in a template to the current settings on a computer. Applying a template ensures that a computer conforms to a specific security configuration. Comparing settings can help you identify any discrepancies between what is implemented currently and what is defined in a security template. This can also be useful to determine whether security settings have changed over time.
REAL WORLD The key drawback to using the Security Configuration And Analysis snap-in is that you cannot configure multiple computers at once. You can configure security only on the computer on which you are running the snap-in. If you want to use this tool to deploy security configurations, you must log on to and run the tool on each computer. Although this technique works for standalone computers, it is not the optimal approach in a domain. In a domain setting, you’ll want to import the security template settings into a Group Policy object (GPO), and then deploy the security configuration to multiple computers. For more information, see “Deploying security templates to multiple computers” later in this chapter.
The Security Configuration And Analysis snap-in uses a working database to store template security settings, and then applies the settings from this database. For analysis and comparisons, the template settings are listed as the effective database settings and the current computer settings are listed as the effective computer settings. Keep in mind that if you are actively editing a template in the Security Templates snap-in, you need to save the template so that the changes can be analyzed and used.
After you create a template or determine that you want to use an existing template, you can analyze and then configure the template by following these steps:
1. Open the Security Configuration And Analysis snap-in.
2. Press and hold or right-click the Security Configuration And Analysis node, and then tap or click Open Database to display the Open Database dialog box.
3. By default, the Open Database dialog box’s search path is set to %SystemDrive%Users%UserName%DocumentsSecurityDatabase. As necessary, select options in the Open Database dialog box to navigate to a new location in which to save the database. In the File Name text box, enter a descriptive name for the database, such as Current Config Comparison, and then tap or click Open. The security database is created in the Security Database Files format with the.sdb file extension.
4. The Import Template dialog box is displayed with the default search path set to %SystemDrive%Users%UserName%DocumentsSecurityTemplates. As necessary, select options in the Import Template dialog box to navigate to a new template location. Select the security template you want to use, and then tap or click Open. Security template files end with the.inf file extension.
5. Press and hold or right-click the Security Configuration And Analysis node, and then tap or click Analyze Computer Now. When prompted to set the error log path, enter a new path or tap or click OK to use the default path.
6. Wait for the snap-in to complete the analysis of the template. If an error occurs during the analysis, you can view the error log by pressing and holding or right-clicking the Security Configuration And Analysis node and choosing View Log File.
When you are working with the Security Configuration And Analysis snap-in, you can review the differences between the template settings and the current computer settings. As Figure 5–9 shows, the template settings stored in the analysis database are listed in the Database Setting column, and the current computer settings are listed in the Computer Setting column. If a setting has not been analyzed, it is listed as Not Defined.
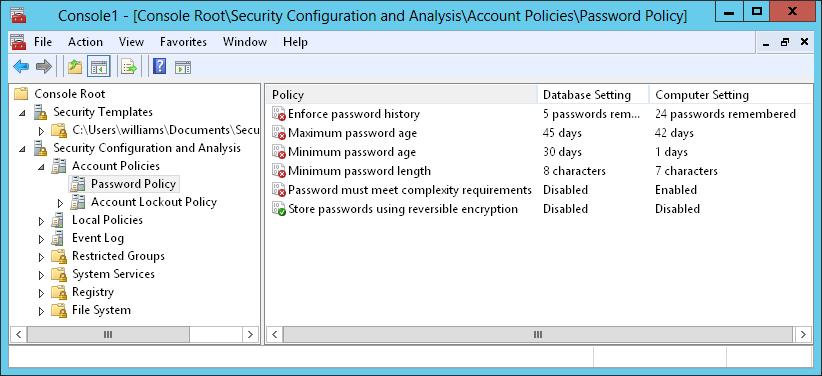
FIGURE 5–9 Review the differences between the template settings and the current computer settings
You can make changes to a setting stored in the database by following these steps:
1. In the Security Configuration And Analysis snap-in, double-tap or double-click the setting with which you want to work.
2. In the Properties dialog box, shown in Figure 5-10, note the current computer setting. If information about the purpose of the setting is available, you can view this information by tapping or clicking the Explain tab.
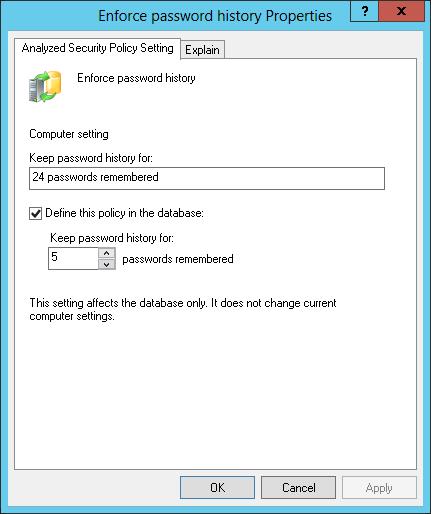
FIGURE 5-10 Change a policy setting in the database before applying the template.
3. To define and apply the policy setting, select the Define This Policy In The Database check box. To clear this policy and not apply it, clear this check box.
4. If you enable the policy setting, specify how the policy setting is to be used by configuring any additional options.
5. Repeat this process as necessary. To save your database changes to the template, press and hold or right-click the Security Configuration And Analysis node, and then tap or click Save.
You can also use the Secedit command-line utility to analyze, review, and apply security templates. The basic technique is as follows:
- Интегрированная безопасность (NT Integrated Security)
- Разработка приложений баз данных InterBase на Borland Delphi
- Open Source Insight and Discussion
- Introduction to Microprocessors and Microcontrollers
- Chapter 6. Traversing of tables and chains
- Chapter 8. Saving and restoring large rule-sets
- Chapter 11. Iptables targets and jumps
- Chapter 5 Installing and Configuring VirtualCenter 2.0
- Chapter 16. Commercial products based on Linux, iptables and netfilter
- Appendix A. Detailed explanations of special commands
- Appendix B. Common problems and questions
- Appendix E. Other resources and links




