Книга: Linux Network Administrator Guide, Second Edition
What Is a Firewall?
What Is a Firewall?
A firewall is a secure and trusted machine that sits between a private network and a public network.[59] The firewall machine is configured with a set of rules that determine which network traffic will be allowed to pass and which will be blocked or refused. In some large organizations, you may even find a firewall located inside their corporate network to segregate sensitive areas of the organization from other employees. Many cases of computer crime occur from within an organization, not just from outside.
Firewalls can be constructed in quite a variety of ways. The most sophisticated arrangement involves a number of separate machines and is known as a perimeter network. Two machines act as "filters" called chokes to allow only certain types of network traffic to pass, and between these chokes reside network servers such as a mail gateway or a World Wide Web proxy server. This configuration can be very safe and easily allows quite a great range of control over who can connect both from the inside to the outside, and from the outside to the inside. This sort of configuration might be used by large organizations.
Typically though, firewalls are single machines that serve all of these functions. These are a little less secure, because if there is some weakness in the firewall machine itself that allows people to gain access to it, the whole network security has been breached. Nevertheless, these types of firewalls are cheaper and easier to manage than the more sophisticated arrangement just described. Figure 9.1 illustrates the two most common firewall configurations.
Figure 9.1: The two major classes of firewall design
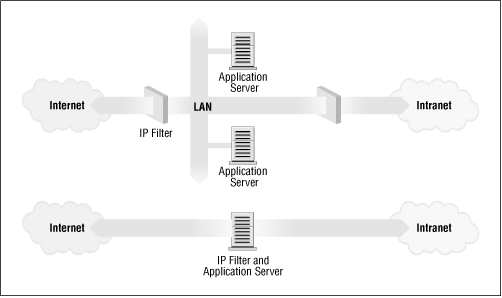
The Linux kernel provides a range of built-in features that allow it to function quite nicely as an IP firewall. The network implementation includes code to do IP filtering in a number of different ways, and provides a mechanism to quite accurately configure what sort of rules you'd like to put in place. The Linux firewall is flexible enough to make it very useful in either of the configurations illustrated in Figure 9.1. Linux firewall software provides two other useful features that we'll discuss in separate chapters: IP Accounting (Chapter 10, IP Accounting) and IP masquerade (Chapter 11, IP Masquerade and Network Address Translation).
- Methods of Attack
- What Is a Firewall?
- What Is IP Filtering?
- Setting Up Linux for Firewalling
- Three Ways We Can Do Filtering
- Original IP Firewall (2.0 Kernels)
- IP Firewall Chains (2.2 Kernels)
- Netfilter and IP Tables (2.4 Kernels)
- TOS Bit Manipulation
- Testing a Firewall Configuration
- A Sample Firewall Configuration
- Chapter 5. Preparations
- Chapter 10. Iptables matches
- Chapter 12. Debugging your scripts
- Chapter 13. rc.firewall file
- Chapter 14. Example scripts
- Chapter 15. Graphical User Interfaces for Iptables
- Chapter 16. Commercial products based on Linux, iptables and netfilter
- What's next?
- IP filtering terms and expressions
- How to plan an IP filter
- Example NAT machine in theory
- What is needed to build a NAT machine




