Книга: Learning GNU Emacs, 3rd Edition
12.3 How VC Helps with Basic Operations
12.3 How VC Helps with Basic Operations
Historically, you had to know three or four different shell commands to do the basic operations of version control (registration, check in, check out, and revert), and you had to do each one outside your editor (or in an editor subshell). This procedure was complicated and annoying, or at best a distraction from the flow of working on your code and changes.
VC's interface is much simpler. The simplicity comes from noticing that whatever state your version-controlled file is in, there is normally just one logical thing to do next. Here are the rules:
• If your file isn't under version control, the next logical thing to do is register it and (where relevant) check out a modifiable copy for you.
• If it's registered, but not checked out by anyone, the next thing you generally want to do is check it out so you can edit it (again, where relevant, such as if you're using CVS in a "keep files read-only unless I say I want to edit them" mode).
• If you have made changes to the file, the next logical thing is to check it back in, which may involve reconciling your changes with those made by someone else.
• Much more rarely, if you're using one of the pre-CVS systems, if someone else has a file checked out, you may want to steal the lock (notifying the lock owner that you've done so).
Indeed, VC mode has just one basic command: C-x v v (for vc-next-action), which you can think of as "do the next logical thing to this file" or, more precisely: "take the currently visited file to the next normal version control state." It follows the arrows in Figure 12-1, which describes the traditional version control cycle.[86] This command is available in every Emacs since 19; when you invoke it, it automatically fetches the rest of VC and does its job.
Figure 12-1. The traditional version control cycle
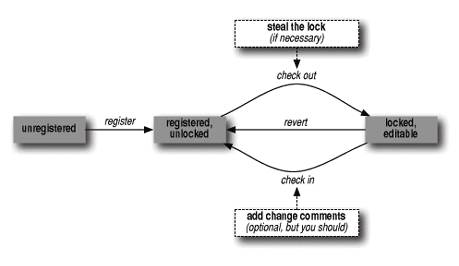
There's a little more to it than that, of course. For one thing, when you check in a set of changes to a file, VC pops up a buffer for you to enter a change comment. Similarly, if you're in an older version control environment, when you steal a lock, VC pops up a buffer requesting an explanation. This explanation is mailed to the lock owner.
VC gives you a revert operation as well: C-x v u (for vc-revert-buffer). Actually, the function that implements vc-next-action checks to see if the buffer is unmodified since check-out time; if so, it offers to revert the buffer and unlocks the work file rather than checking in an empty change.
Although it's worth understanding this traditional flow because it's how VC is designed, working with today's concurrent version control systems is slightly different. Luckily, it's even a little simpler. Because there is no need to obtain a lock in order to edit a document, one of the VC steps is missing (or, if you prefer, you can think of it as implicit). This is illustrated in Figure 12-2.
Figure 12-2. The concurrent version control cycle
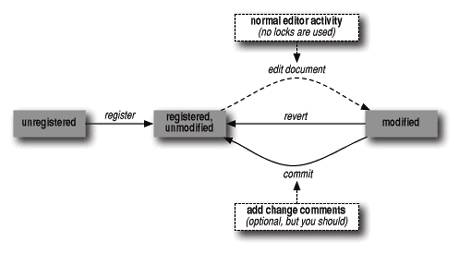
The transition from the unmodified state to the modified state (with respect to the version in the repository) is shown as a dotted line, because you no longer perform a VC operation here. You just start editing the file you want to work with. Whenever you tell VC you want the "next action" it's able to tell whether the document is modified or not. If it is, the current version is committed ("checked in," if you will) and you're prompted for the change comments. If the file is registered but unmodified, VC simply displays a message in the minibuffer telling you that the buffer is up to date.
If you prefer to configure CVS to give you read-only versions of files until you explicitly choose to edit them, your workflow will remain that of Figure 12-1.
- 12.1 The Uses of Version Control
- 12.2 Version Control Concepts
- 12.3 How VC Helps with Basic Operations
- 12.4 Editing Comment Buffers
- 12.5 VC Command Summary
- 12.6 VC Mode Indicators
- 12.7 Which Version Control System?
- 12.8 Individual VC Commands
- 12.9 Customizing VC
- 12.10 Extending VC
- 12.11 What VC Is Not
- 12.12 Using VC Effectively
- 12.13 Comparing with Ediff
- 8.5.2 Typical Condition Variable Operations
- How to read
- Chapter 9. How a rule is built
- How it was written
- How to plan an IP filter
- What NAT is used for and basic terms and expressions
- Using Double Quotes to Resolve Variables in Strings with Embedded Spaces
- chown
- How to place proxies
- Drawbacks with restore
- Basics of the iptables command
- 7. AGGREGATION WITH INDEPENDENT WORKS




